What is a Slowloris DDoS attack?
Slowloris is a type of DDoS (Distributed Denial of Service) attack that exploits web servers to handle incoming connections.
In a Slowloris attack, the attacker sends many HTTP requests to the target web server, but unlike a regular DDoS attack, the requests are sent slowly over a long period of time.
The attack sends incomplete HTTP requests to keep the connections open for as long as possible. The attacker then mimics this pattern by sending many incomplete requests to the server. By doing this, the attacker consumes the server’s memory and CPU as it tries to keep track of all the open connections. Eventually, the server becomes overwhelmed and can no longer respond to legitimate requests.
Examples of Slowloris Attacks
There have been several high-profile Slowloris attacks over the years. Here are a few examples:
- In 2009, Iran accused the US of launching Slowloris attacks against its government websites. The attack lasted for several weeks and caused significant disruption to the targeted sites.
- In 2011, the website of the CIA was reportedly targeted by a Slowloris attack by the hacker group LulzSec. The attack caused the website to be unavailable for several hours.
- In 2018, a Slowloris attack was launched against several banks in Russia, causing their websites to become inaccessible. The attack was reportedly carried out by a group of hackers known as MoneyTaker.
How is a Slowloris DDoS attack different when compared to a traditional application DDoS attack?
Slowloris DDoS attacks are different from traditional DDoS attacks in a couple of ways.
First, in a traditional application DDoS attack, the attacker floods the target with a huge number of requests, typically from botnets. These requests can be legitimate or malicious and are designed to overwhelm the target’s resources, such as memory or CPU.
In contrast, in a Slowloris attack, the attacker sends a relatively small number of requests but does so slowly and incrementally. These requests consume the target’s resources over a longer period of time. The requests are typically incomplete, with the attacker deliberately keeping the connection open by sending partial requests or delaying sending the next request.
Finally, traditional application DDoS attacks are often detected and mitigated by WAFs or intrusion prevention systems, while Slowloris attacks can be more difficult to detect and block. The attack traffic may not appear malicious, and the server may appear functioning normally, even when overloaded with open connections.
Why Are Slowloris DDoS Attacks Dangerous?
Slowloris DDoS attacks are dangerous because they can be carried out with relatively few resources and can effectively take down even large and robust web servers.
Slowloris attacks are called “slow” because they don’t rely on sending a high traffic volume like other DDoS attacks but rather on keeping a low-level stream of connections open for as long as possible.
As logs cannot be written until a request is completed, Slowloris can immobilize a server and go undetected for a long time. This happens without raising a red flag for anyone who actively monitors logs for any changes.
Because Slowloris attacks only require a small amount of bandwidth and can be carried out by a single machine, they are often difficult to detect and defend against.
Overall, Slowloris DDoS attacks are dangerous because they can be highly effective at taking down web servers, are difficult to detect and defend against, and can be launched with minimal resources.
How does a Slowloris Attack Work?
Here is a step-by-step process of how a Slowloris attack is carried out
- The attacker identifies a target web server.
- The attacker uses a script, generally written in Python or Perl, to open multiple connections to the target server.
- Instead of sending complete HTTP requests, the attacker sends partial requests to the server. These requests typically consist of a request header but no request body.
- The attacker sends these partial requests quite slowly. Usually, with a delay of several seconds between each request. This is done to keep the connection to the server open for as long as possible.
- The attacker keeps the connection open by continuing to send partial requests. These requests occupy server resources such as memory and CPU time.
- The server becomes overwhelmed as the number of open connections increases and cannot handle legitimate requests from other clients.
- The website or web application hosted on the server becomes slow or unresponsive or may even crash entirely.
- The attacker can continue to maintain the Slowloris attack for an extended period of time, causing significant damage to the targeted server.
For example:
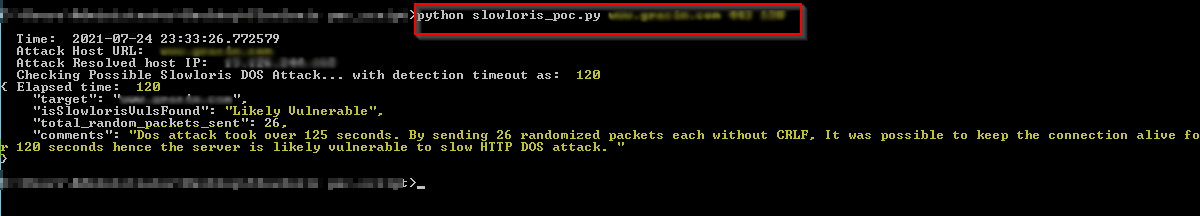
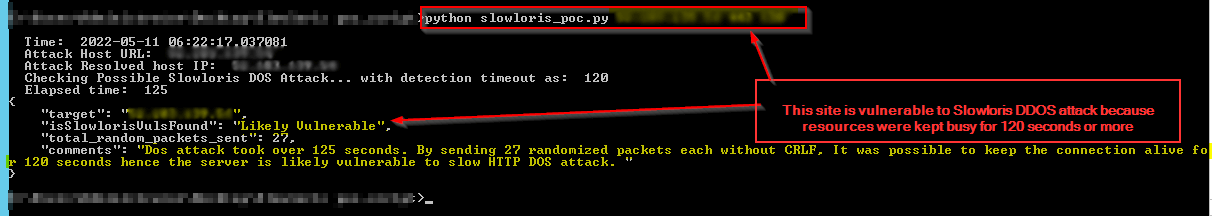
Overall, the Slowloris DDoS attack exploits a vulnerability in how web servers handle connections, using a slow but persistent stream of partial requests to tie up server resources and make the server unavailable to legitimate users.
How to Mitigate and Prevent a Slowloris DDoS Attack?
Here are six ways to mitigate and prevent a Slowloris DDoS attack:
1. Use a reverse proxy
A reverse proxy would act as a buffer between the server and clients, protecting the server from Slowloris attacks. The reverse proxy should ideally monitor incoming requests and drop connections that show signs of a Slowloris attack.
2. Limit # connections per IP
Limiting the number of connections that can be made from a single IP address would reduce the impact of a Slowloris attack. You could easily do this with a cloud WAF like AppTrana or a load balancer.
3. Reduce the maximum request duration
Limiting the time a connection can be kept open would reduce the impact of a Slowloris attack. You could easily do this with a cloud WAF like AppTrana, a load balancer, or setting a timeout.
4. Implement rate limiting
By monitoring the number of connections and requests made to the server and limiting them to a reasonable threshold, the impact of a Slowloris attack can be mitigated. This can be achieved using software or hardware solutions, such as load balancers, firewalls, or intrusion prevention systems.
5. Keep software and systems up to date
Keeping web server software and operating systems up to date can help prevent known vulnerabilities that Slowloris attacks can exploit. Leverage a DAST scanner like Indusface WAS to find all open vulnerabilities categorized by OWASP Top 10 and SANS 25.
6. Use a DDoS mitigation service
Specialized DDoS mitigation services can protect against Slowloris and other DDoS attacks. The AppTrana cloud WAF comes with bundled managed services to help you with custom rate limiting, traffic filtering, and traffic diversion to protect servers and networks from DDoS attacks.
How does AppTrana Protect Against Slowloris Attacks?
AppTrana offers the industry’s only unmetered anti-DDoS solution backed by AI-based behavioural models that detect anomalies on site traffic. The cloud WAF also bundles managed services wherein cutting-edge technology is combined with the power of human expertise and intelligence of certified security professionals. It is a comprehensive security solution that is custom-built with surgical accuracy based on the needs and risk profile of the business.
AppTrana’s security services include infrastructure-level protection against volumetric Layer 3 and 4 attacks and always-on, instant protection against Layer 7 attacks by botnets and attacks like Slowloris on the application layer. AppTrana monitors websites and web applications 24×7 to detect anomalous activities. The security experts continuously update the rules in real-time based on alerts to mitigate DDoS attacks and ensure web application/ website available at all times.
Stay tuned for more relevant and interesting security updates. Follow Indusface on Facebook, Twitter, and LinkedIn

The post What is a Slowloris DDoS attack? appeared first on Indusface.
*** This is a Security Bloggers Network syndicated blog from Indusface authored by Venkatesh Sundar. Read the original post at: https://www.indusface.com/blog/what-is-slowloris/



