Implementing MITRE D3FEND for ATT&CK Technique T1110: Brute Force
When account credentials are unknown, attackers may use a brute force attack in order to gain access. This can occur as an early stage of their attack, to gain initial access, or to enhance their privileges after access has already been obtained. MITRE’s D3FEND matrix outlines how to address this technique; however, security teams struggle to consistently implement D3FEND’s recommendations.
This blog demonstrates how Security Orchestration, Automation, and Response (SOAR) can be used to consistently implement the final three stages of the D3FEND framework to respond to brute force attacks.
The D3FEND Matrix
The MITRE D3FEND Matrix has six stages: model, harden, detect, isolate, deceive, and evict. Within each stage are specific tasks that when performed can successfully detect, contain, and recover from brute force attacks. Here is how Smart SOAR can be used to automate the tasks recommended by MITRE in the isolate, deceive, and eviction stages:
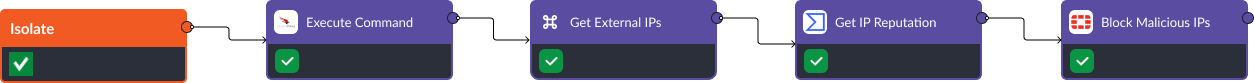
Isolate
D3FEND Recommendation: Network Traffic Filtering. In the isolation stage, the incident response team must restrict incoming and outgoing traffic from any suspicious endpoint. Here, we use a combination of tools including CrowdStrike, VirusTotal, and FortiGate Next-Generation Firewall (NGFW) to automate this process across four steps:
- Execute Command: This CrowdStrike command lets us remotely execute scripts on select devices. In this workflow, we use this command to retrieve a comprehensive list of all TCP connections made by our affected device.
- Get External IPs: Using this built-in command, we can extract TCP connections made to devices outside of the corporate network for analysis later.
- Get IP Reputation: This task queries VirusTotal’s threat intelligence database to retrieve the reputation of all external IPs found in the previous step. VirusTotal aggregates information from various security sources and provides insight into whether an IP is associated with malicious activities, such as hosting malware, phishing sites, or other threats. This task assists in determining the risk level posed by an IP address and informs our final action in the workflow.
- Block Malicious IPs: This task makes changes to the FortiGate NGFW blocklist to prevent any communication to or from malicious IPs identified by VirusTotal.
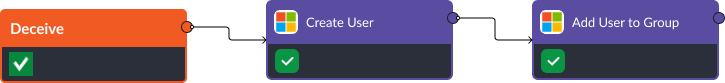
Deceive
D3FEND Recommendation: Decoy User Credential. Various identity and access management (IAM) tools can be used within Smart SOAR to create user accounts that are designed to deceive hackers and notify the security team when a breach has occurred. In this example, we use Azure Active Directory to create a user and assign them to a benign group. Then, we run a scheduled automation to check the activity logs of that user and create an incident when a login is detected.
Scheduled automations are playbooks that are run on a timed cadence, such as once a week or once a month.
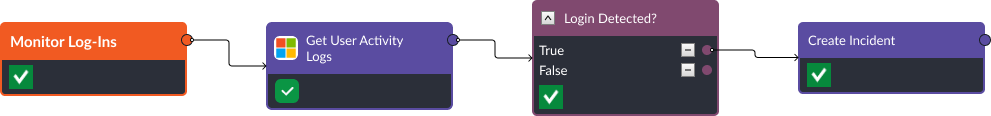
These playbooks are not triggered by security alerts ingested into the platform, rather, they continue operating in the background and are useful for proactive threat hunting.
Read: What Are MITRE ATT&CK and MITRE D3FEND?
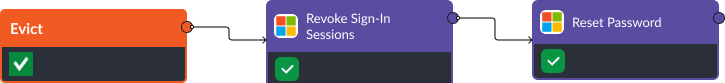
Evict
D3FEND Recommendation: Authentication Cache Invalidation. The final stage of the D3FEND framework is eviction. If a user’s account has been compromised, IAM tools can be used to repair their accounts. In this case, Active Directory’s Revoke Sign-In Sessions command forcibly ends an existing user’s sessions across various devices and applications. When this task is executed, all active authentication sessions for a specific user are immediately invalidated, requiring users to re-authenticate.
D3FEND Recommendation: Credential Revoking. In combination with the Revoke Sign-In Sessions command, Active Directory’s Reset Password command can be used to change the user’s password to a new, temporary one. When the user has logged back in, they may be prompted to create a new, unique password. This ensures that the account remains secure and is only accessible by authorized individuals.
Takeaway
In this example we used CrowdStrike, VirusTotal, Fortinet, and Active Directory to respond to a brute force attack following MITRE D3FEND’s best practices. With unlimited integrations, Smart SOAR can enable similar workflows using any common tools in these categories. SOAR tools are particularly helpful in the isolation, deception, and eviction stage, as they are able to take action in any environment your security team has access to.
The post Implementing MITRE D3FEND for ATT&CK Technique T1110: Brute Force appeared first on D3 Security.
*** This is a Security Bloggers Network syndicated blog from D3 Security authored by Pierre Noujeim. Read the original post at: https://d3security.com/blog/implementing-mitre-d3fend-for-attck-technique-t1110-brute-force/



