Why Smart SOAR is the Best Independent SOAR for Splunk Enterprise Security
Connecting Splunk SIEM with other security tools is a scenario Smart SOAR handles often. By ingesting alerts from Splunk into Smart SOAR, and using the integration commands in event and incident playbooks, Smart SOAR users can leverage Splunk’s database in incident investigations by consolidating all relevant information on an event. The same enrichment can be done on security alerts generated by other tools that may not have data from Splunk included.
The commands enabled by Smart SOAR’s Splunk integration are:
- Add Threat Intel Collection Row
- Create Event
- Delete Threat Intel Collection Row
- Fetch Event
- Get Application List
- Get Lookup Table Content
- Get Recent Notable Events
- Get Search Result
- Get Search Status
- Get Status List
- List Indexes
- List Lookup Table Files
- List Threat Intel Collection Rows
- Search
- Start Search
- Submit Event
- Update Notable Events
- Upload Files
- Upload Lookup Tables
Below, I will outline four ways to leverage these commands in incident response playbooks.
Data Ingestion
Three types of events can be ingested into Smart SOAR from Splunk: Generic, Notable, and Windows Event Logs. Each has a field-mapping schema that is dynamically assigned to incoming alerts based on the type of event to ensure all events are normalized when entering Smart SOAR. By ingesting alerts into Smart SOAR, users can centralize all security alerts onto a single platform. Alerts from endpoint, network, and email security tools can be combined into a single queue.
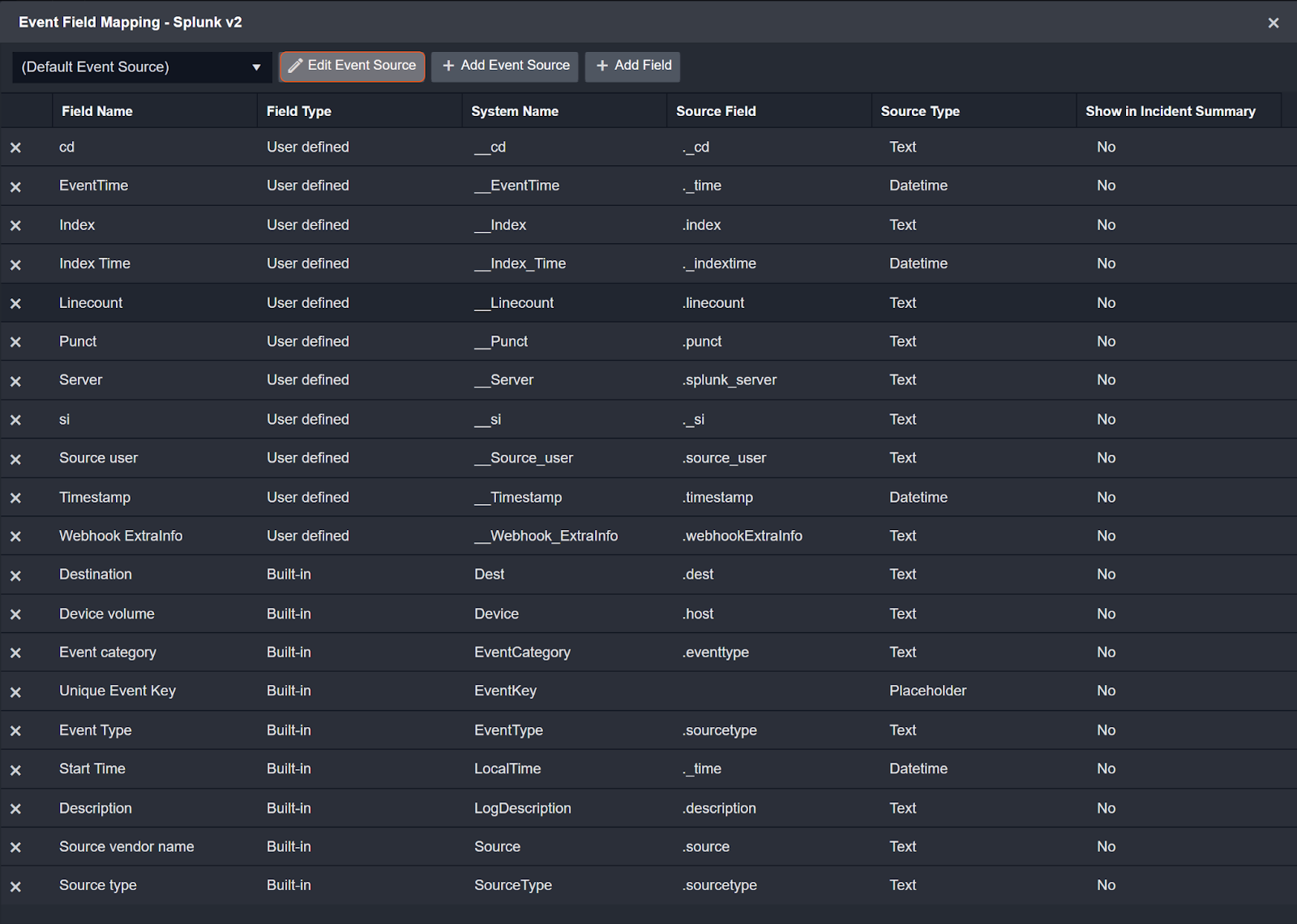
Field Mapping for Generic Events
Searching
Following Splunk’s search syntax, users can initiate searches and retrieve the results directly from Smart SOAR using the following commands:
- Start Search
- Get Search Status
- Get Search Result
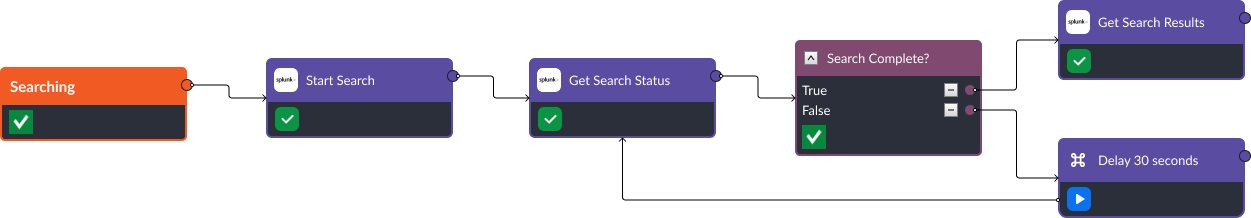
These searches can be executed when alerts are ingested from different security tools, and users want to query Splunk’s database for information on artifacts such as devices, users, and IP addresses.
Data Enrichment
The Get Application List, Get Lookup Table Content, and List Threat Intel Collection Rows commands are common data enrichment commands that can help inform future Splunk search queries and next steps. Data enrichment is a common step in the incident response process when using Smart SOAR because of its ability to quickly consolidate all relevant information on an incident.

Updating Splunk
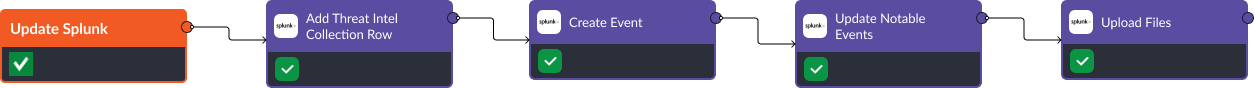
When changes are made to active incidents, it’s common for security analysts to need to update the original alert in order to maintain consistency. Using the Update Notable Events command, users can accomplish this within playbooks.
Additional write-actions can be performed on Splunk from Smart SOAR, including Add Threat Intel Collection Row, Create Event, and Upload Files.
Takeaway
The integration between Splunk Enterprise Security and Smart SOAR gives users the opportunity to integrate Splunk with tools from hundreds of vendors. Security teams that are handling half-a-dozen or more security tools benefit greatly from these vendor-agnostic integration capabilities. Splunk is a large and valuable database that can provide key contextual information on security alerts and artifacts. By leveraging this integration, users can automate data collection, searching, platform synchronization to quicken their time to mitigate on every alert.
The post Why Smart SOAR is the Best Independent SOAR for Splunk Enterprise Security appeared first on D3 Security.
*** This is a Security Bloggers Network syndicated blog from D3 Security authored by Pierre Noujeim. Read the original post at: https://d3security.com/blog/smart-soar-splunk-integration-guide/



