How to Use MITRE ATT&CK in 2023: A Must-Read Guide
Introduction
In 2023, cybersecurity remains a pressing concern for businesses big and small. At the heart of this ever-evolving landscape is the MITRE ATT&CK framework. Designed to arm IT professionals with actionable insights, this framework is more relevant than ever.
MITRE ATT&CK serves as a comprehensive guide for understanding the complex tactics and techniques employed by cyber adversaries. So, why is MITRE ATT&CK crucial for your business this year? Let’s unravel the mystery.
The Evolution of MITRE ATT&CK
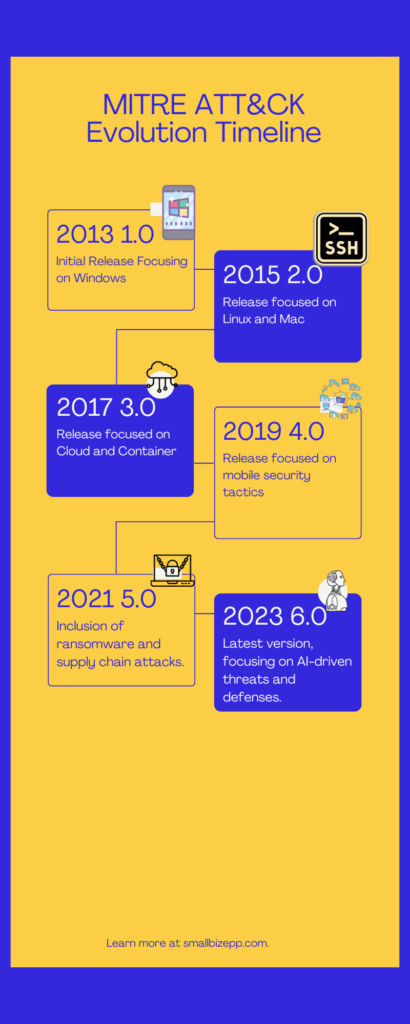
Since its inception as a tool for understanding cyber adversary behavior, the MITRE ATT&CK framework has evolved significantly. Since then, it has expanded its scope to become a comprehensive guide for cybersecurity. Over the years, it has undergone several updates, each adding new layers of complexity and utility.
In 2023, the framework is more relevant than ever. With the rise of AI-driven cyber threats, the latest version aims to equip businesses with the tools to counteract these advanced attacks. It’s not just about understanding your enemy anymore; it’s about staying one step ahead.
Why Understanding MITRE ATT&CK is Crucial for Small Businesses
In today’s digital age, small businesses are not immune to cyber threats. In fact, they often become easy targets for cyber attackers due to limited resources and expertise. Budget constraints often mean less investment in cybersecurity measures, leaving gaping holes in the defense system.
Enter MITRE ATT&CK. This framework isn’t just for large enterprises; it’s a boon for small businesses too. By understanding its core components—tactics, techniques, and procedures—you can effectively identify vulnerabilities and fortify your defenses without breaking the bank.
MITRE ATT&CK demystifies the complex world of cybersecurity. It provides actionable insights that even those with limited cybersecurity knowledge can understand and implement. From threat detection to red teaming, the framework offers a roadmap to navigate the treacherous waters of cyber threats.
So, if you’re a small business grappling with budget limitations and cybersecurity concerns, MITRE ATT&CK is your go-to guide for a more secure 2023.
Core Components of MITRE ATT&CK
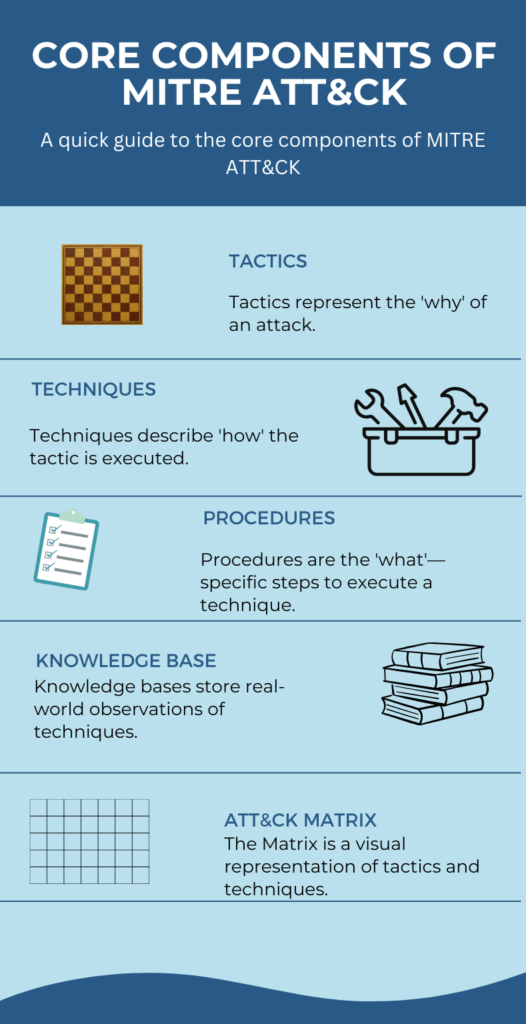
Understanding the core components of MITRE ATT&CK is crucial for effective cybersecurity. These components serve as the building blocks of the framework, each with its unique role and function.
Tactics, Techniques, and Procedures (TTPs)
Tactics represent the “why” of an attack—the adversary’s objectives. Techniques are the “how”—the methods employed to achieve these objectives. Procedures are the “what”—specific actions taken using those methods. Together, these TTPs provide a comprehensive view of potential cyber threats, allowing you to prepare and defend accordingly.
ATT&CK Matrix
The Mitre ATT&CK Matrix is a visualization tool that maps out various tactics and techniques. It serves as a guide for identifying potential vulnerabilities and planning defenses. Each cell in the matrix corresponds to a specific technique under a broader tactic, making it easier to pinpoint areas of concern.
Knowledge Base
The Knowledge Base is a rich repository of information that supports the ATT&CK Matrix. It includes detailed descriptions of tactics, techniques, and real-world examples. Security teams often use it as a reference for threat detection and response planning.
By understanding these core components, you’re better equipped to navigate the complex landscape of cybersecurity. Refer to the accompanying graphic for a visual breakdown of these elements.
Real-world Applications of MITRE ATT&CK
The MITRE ATT&CK framework isn’t just a theoretical model; it has practical applications that can significantly enhance your cybersecurity measures. Below, we explore three key use-cases where ATT&CK proves invaluable.
Cyber Threat Intelligence
Understanding the tactics and techniques of potential threat actors is crucial. ATT&CK helps you build a robust cyber threat intelligence program. It allows you to identify the modus operandi of adversaries, thereby enabling proactive defense measures.
Detection and Response
In the realm of detection and response, ATT&CK serves as a guide for monitoring network traffic and user behavior. It helps security teams to identify anomalies and take swift action. The framework provides a structured approach to detect, analyze, and respond to various cyber threats.
Red Teaming and Penetration Testing
For those involved in red teaming and penetration testing, ATT&CK is a treasure trove. It helps in identifying vulnerabilities in your system and testing your defenses against simulated attacks. The framework offers a roadmap for ethical hackers to evaluate the effectiveness of security measures.
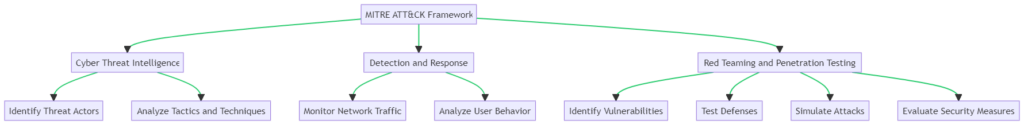
By applying MITRE ATT&CK in these scenarios, you’re not just reacting to cyber threats but proactively managing them. Refer to the accompanying flowchart for a visual guide on how to implement ATT&CK in these real-world applications.
Community Contributions: The Backbone of ATT&CK
The MITRE ATT&CK framework isn’t just a product of a few cybersecurity experts; it’s a community-driven initiative. Security professionals, researchers, and organizations contribute by sharing insights, tactics, and techniques. This collaborative approach keeps the framework updated and relevant.
Open-Source Tools: ATT&CK Navigator and More
One of the most notable open-source tools is the ATT&CK Navigator. This web-based interface allows you to customize the ATT&CK Matrix according to your needs. It’s an invaluable resource for planning, executing, and reviewing your cybersecurity strategy.
Why Community and Open Source Matter
The community-driven aspect and open-source tools like ATT&CK Navigator make the framework adaptable and up-to-date. They foster a sense of collective responsibility and innovation in cybersecurity, making it more than just a tool—it’s a community.
By leveraging community contributions and open-source tools, you’re not just using a framework; you’re becoming part of a global effort to enhance cybersecurity.
How to Implement MITRE ATT&CK Effectively
Implementing the MITRE ATT&CK framework can seem daunting, but breaking it down into manageable steps makes the process achievable. Below is a comprehensive guide to help you navigate this journey, ensuring a robust cybersecurity posture for your organization.
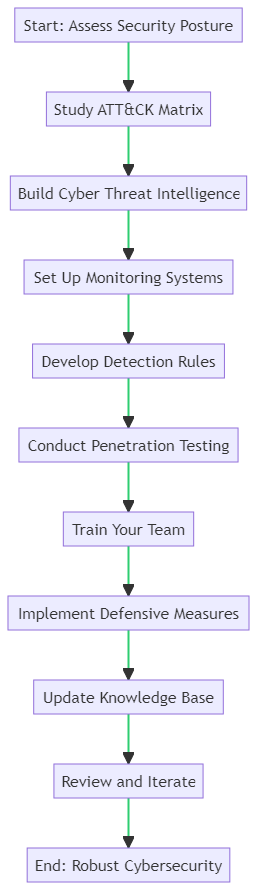
Step 1: Assess Your Current Security Posture
Before diving into the framework, evaluate your existing security measures. Identify gaps and areas for improvement.
Step 2: Familiarize Yourself with the ATT&CK Matrix
Study the ATT&CK Matrix to understand the tactics and techniques that adversaries may use. This will serve as your roadmap.
Step 3: Build Your Cyber Threat Intelligence
Utilize the framework to identify potential threat actors and their tactics. Create profiles for different types of cyber threats.
Step 4: Set Up Monitoring Systems
Implement monitoring systems to track network traffic and user behavior. Use the framework as a guide for what to look for.
Step 5: Develop Detection Rules
Based on your understanding of tactics and techniques, develop detection rules. These will trigger alerts for suspicious activities.
Step 6: Conduct Penetration Testing
Use the framework to simulate attacks on your system. This will help you identify vulnerabilities and test your defenses.
Step 7: Train Your Team
Ensure that your security team is well-versed in the framework. Conduct regular training sessions and drills.
Step 8: Implement Defensive Measures
Based on your findings, implement defensive measures. This could range from firewalls to endpoint security solutions.
Step 9: Continuously Update Your Knowledge Base
The cyber landscape is ever-changing. Keep your knowledge base updated with the latest tactics and techniques.
Step 10: Review and Iterate
Regularly review the effectiveness of your security measures. Make necessary adjustments and iterate on your security strategy.
By following these steps, you’ll be well on your way to implementing a robust cybersecurity strategy using the MITRE ATT&CK framework.
Using MITRE ATT&CK as a Benchmark
The MITRE ATT&CK framework serves as a comprehensive benchmark for evaluating various cybersecurity measures. It’s particularly useful for small businesses aiming to enhance their security posture without exceeding their budget.
Why ATT&CK is Crucial for Cybersecurity
The framework offers a detailed list of adversarial tactics, techniques, and procedures (TTPs). This enables businesses to understand the threat landscape and make data-driven decisions.
Endpoint Security: A Special Focus
Given the rise in remote work and BYOD policies, endpoint security has become a focal point. Using the ATT&CK framework, businesses can evaluate how well a product can defend against specific tactics like “privilege escalation” and “defense evasion.”
Questions to Ask Vendors
Before investing, inquire how vendors’ products align with ATT&CK techniques. Ask for real-world examples or case studies to ensure the product meets your specific needs.
Budget Considerations
Budget constraints are a reality for small businesses. Look for modular pricing or tiered features that allow you to scale your security measures as your business grows.
By using the MITRE ATT&CK framework as a benchmark, you can make well-informed decisions that align with your cybersecurity needs and budget.

Common Pitfalls and How to Avoid Them
Implementing the MITRE ATT&CK framework is a complex process, and it’s easy to stumble along the way. Awareness of these pitfalls can save you time, money, and potential security risks.
Overlooking the Basics
One common mistake is jumping into advanced tactics and techniques without a solid grasp of the basics. Ensure your team understands the core components of the framework before diving deeper.
Ignoring Budget Constraints
While it’s tempting to go for the most comprehensive security solutions, it’s crucial to stay within budget. Opt for modular solutions that allow you to add features as needed.
Inadequate Training
A framework is only as good as the people using it. Regular training sessions and drills are essential for effective implementation.
Neglecting to Update
The cyber threat landscape is ever-changing. Failing to update your knowledge base and adjust your strategy accordingly is a recipe for disaster.
Over-Reliance on Tools
While tools like the ATT&CK Navigator are invaluable, they shouldn’t replace human judgment. Always corroborate tool-based insights with manual analysis.
By being aware of these common pitfalls and following best practices, you can implement the MITRE ATT&CK framework more effectively and securely.
Conclusion: Future of MITRE ATT&CK and Your Business
The MITRE ATT&CK framework is more than just a cybersecurity tool; it’s a roadmap for navigating the complex landscape of cyber threats. Its importance and relevance will only grow as we move further into the digital age. For those interested in defensive measures, MITRE has also introduced D3FEND, a complementary framework focused on defensive techniques.
Don’t just read about ATT&CK—start implementing it in your cybersecurity strategy today. And if you have questions or need clarification, feel free to ask. Your security posture can only benefit from this comprehensive framework.
The post How to Use MITRE ATT&CK in 2023: A Must-Read Guide appeared first on Endpoint Security.
*** This is a Security Bloggers Network syndicated blog from Endpoint Security authored by Michael Toback. Read the original post at: https://smallbizepp.com/how-to-use-mitre-attack/?utm_source=rss&utm_medium=rss&utm_campaign=how-to-use-mitre-attack



