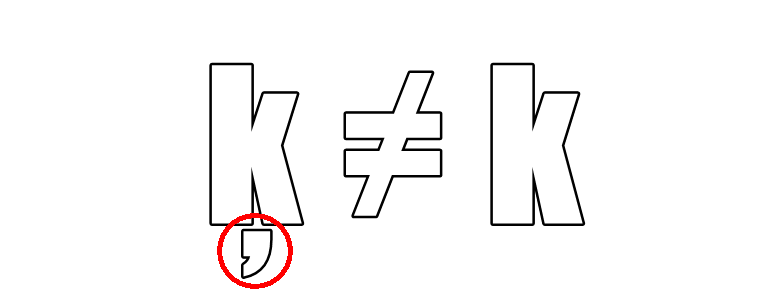Stay current with latest developments in the hacking world. Explore topics, ranging from threats and breaches including data breaches to password hacks to malware. Readers can find posts updated hourly covering incidents around the world authored by some of leading experts and contributors in Cybersecurity industry.

Palo Alto Networks Extends Scope of CNAPP Reach
Via a Darwin update, Palo Alto Networks this week added six capabilities to its cloud-native application protection platform (CNAPP) ...
Security Boulevard

KeePass Malicious Ads: Google Goof Permits Punycode Attacks Again
Richi Jennings | | IDN, IDN homograph phishing, internationalized domain names, KeePass, Punycode, SB Blogwatch
Mote below k: Not only malvertising, but also “verified by Google.” ...
Security Boulevard

U.S. Seizes Money, Domains Involved In North Korea IT Worker Scam
U.S. law enforcement agencies over the past year seized 17 web domains and almost $1.5 million as part of an ongoing effort to shut down a North Korean program to plant IT ...
Security Boulevard

Survey Sees Zero-Trust Transition Gaining Momentum
A recent Okta survey found the majority of organizations have implemented a zero-trust IT initiative, with another 35% planning to do so soon ...
Security Boulevard

How to Make Your Threat-Hunting Program More Effective
As threats increase, here are three ways to improve the effectiveness and success of your organization's threat-hunting program ...
Security Boulevard

Dependency mapping: A beginner’s guide
Aaron Linskens | | Application Security, dependencies, open source, software supply chain, Vulnerabilities
Organizations everywhere use open source to expedite development, lower costs, and improve performance. Our annual State of the Software Supply Chain reports consistently reaffirm that open source comprises up to 90% of ...

What are the Different Types of VAPT Services?
Vulnerability Assessment and Penetration Testing (VAPT) services primary goal is to enhance digital security. The potential for cyber threats and vulnerabilities is constantly growing. This is where VAPT services step in, taking ...
The Role of IoT Vulnerabilities in Identity Theft: An Unseen Danger for High-Net-Worth Individuals (HNWI)
The Internet of Things (IoT) is transforming how we live and work. From smart homes to connected cars, IoT devices are embedding themselves into our daily lives. But as we embrace this ...

Use of QR Codes in Phishing Campaigns is on the Rise
QR codes are quickly becoming a favorite tool of bad actors looking to launch phishing attacks, with one cybersecurity vendor saying the strategy appeared in 22% of phishing campaigns it detected in ...
Security Boulevard

Cybersecurity Spending Slows as Investment Patterns Shift
There was a 65% drop in growth in cybersecurity spending during the 2022-23 budget cycle, according to an IANS report ...
Security Boulevard