KeePass Malicious Ads: Google Goof Permits Punycode Attacks Again
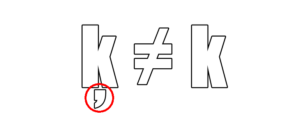 Not only malvertising, but also “verified by Google.”
Not only malvertising, but also “verified by Google.”
Google’s under fire for serving malicious ads for KeePass, even though it “verified” the creator. We thought the IDN/Punycode menace had been quashed, but it appears not—the ads serve a data-stealing Trojan.
The rogue Latvian glyph looks like a speck of dust on your screen—under the ķ. In today’s SB Blogwatch, we blow it off.
Your humble blogwatcher curated these bloggy bits for your entertainment. Not to mention: Happy 50th, SOH.
Mote Below K
VVhāt’š thē črāīč? Jérôme Segura broke the story—“Clever malvertising attack”:
“FakeBat malware”
we observed a malicious Google ad for KeePass, the open-source password manager which was extremely deceiving. … The malicious actors registered a copycat internationalized domain name … to masquerade as the real KeePass site. The difference between the two sites is visually so subtle it will undoubtedly fool many people.
…
The malicious advert shows up when you perform a Google search for ‘keepass’, the popular open-source password manager. The ad is extremely deceiving as it features the official KeePass logo, URL and is featured before the organic search result for the legitimate website.
…
While the decoy site is not an exact replica of the real one, it still looks very convincing. … Extracting the installer’s content reveals malicious PowerShell code that belongs to the FakeBat malware family.
“Internationalized domain name”? Bill Toulas explains—“Fake KeePass site uses Google Ads”:
“ķeepass”
A Google Ads campaign was found pushing a fake KeePass download site … to distribute malware. … Even worse, Google Ads can be abused to show the legitimate domain for Keepass in the advertisements … making the threat hard to spot even for more diligent and security-conscious users.
…
The abuse of Punycode for cybercrime isn’t novel. However, its combination with Google Ads abuse can signify a new dangerous trend in the field. … Punycode is an encoding method used to represent Unicode characters, helping convert hostnames in non-Latin scripts (Cyrillic, Arabic, Greek, Chinese, etc.) to ASCII.
…
Threat actors abuse Punycode to register domain names that appear similar to legitimate sites but with one character using unicode, to look slightly different. These types of attacks are called “homograph attacks.” [These] threat actors use the Punycode “xn—eepass-vbb.info“—which converts to “ķeepass.info,” the project’s genuine domain, but with a [diacritic] underneath the character.
And Dan Goodin did the math—“Google-verified advertiser + legit-looking URL + valid TLS cert = convincing lookalike”:
“Verified by Google”
There’s no way to know that it’s fake. It’s on Google, after all, which claims to vet the ads it carries.
…
Google’s Ad Transparency Center shows that the ads have been running since Saturday and last appeared on Wednesday. The ads were paid for by … Digital Eagle … an advertiser whose identity has been “verified by Google.”
Verified by Google? johnklos rolls his eyes:
Of course they were verified by Google: Google verifies identity by accepting money. Give them money, and you’re verified.
…
Honestly, it’s time for the world to move on from Google. They haven’t been safe to use as a search engine for more than two years.
And who gave the scammers a TLS certificate? FeelGood314 feels bad:
Let’s Encrypt signed the cert. Getting a certificate from Let’s Encrypt is completely automated. … They are terrible for allowing lookalike sites.
…
I think support for non English ASCII characters in URLs is too big of a security risk. Maybe Let’s Encrypt shouldn’t sign certs for Punycode URLs?
Lousy timing. u/Karthanon has news for la GOOG:
Google: “Remove your ad blockers or else you can’t visit this site!”
…
Are you ****ing stupid? … This is one of the reasons we use ad blockers, Google!
This problem is more than 20 years old. jdale ridicules everyone involved:
Proof of concept for abusable non-Latin character URLs was done in 2001. … Ridiculous that this is still allowed. The URL shouldn’t be valid, the browser shouldn’t display it that way, and the ad should have flagged human review at Google. Everyone failed.
Wait. Pause. Not so fast—jasode says it was fixed six years ago:
Google Chrome 59 supposedly fixed the Punycode phishing attack. … Maybe a dedicated criminal studied the Chromium source code that checks Punycode and noticed a flaw where it would allow ‘ķ’ in place of ‘k’?
https://www.xn--80ak6aa92e.com/ –> fake “аррӏе.com” triggers phishing warning,
https://xn--eepass-vbb.info/ –> fake “ķeepass.info” does not trigger warning.
Meanwhile, this Anonymous Coward waxes prurient:
Keep Ass? Nope, thanks to Google’s negligence you’re going to lose it.
And Finally:
“Build your box and stay in it”
You have been reading SB Blogwatch by Richi Jennings. Richi curates the best bloggy bits, finest forums, and weirdest websites … so you don’t have to. Hate mail may be directed to @RiCHi, @richij or [email protected]. Ask your doctor before reading. Your mileage may vary. Past performance is no guarantee of future results. Do not stare into laser with remaining eye. E&OE. 30.